1. K3s指定集群管理IP 在k3s.service中添加启动参数
1 --advertise-address=<192.168.x.x>
详细参考官方文档 以及 K3S安装
查看当前Context
1 kubectl config current-context
2. 配置集群信息 查看context列表
1 kubectl config get-contexts
输出中带有*的Context表示当前活动的Context
切换到指定Context
1 2 3 4 5 kubectl config use-context <context_name> kubectl config use-context dev-ctx
在指定Context中执行命令,一般用于临时使用
1 2 3 4 kubectl --context=<context_name> <exec_cmd> kubectl --context=dev-ctx get pods
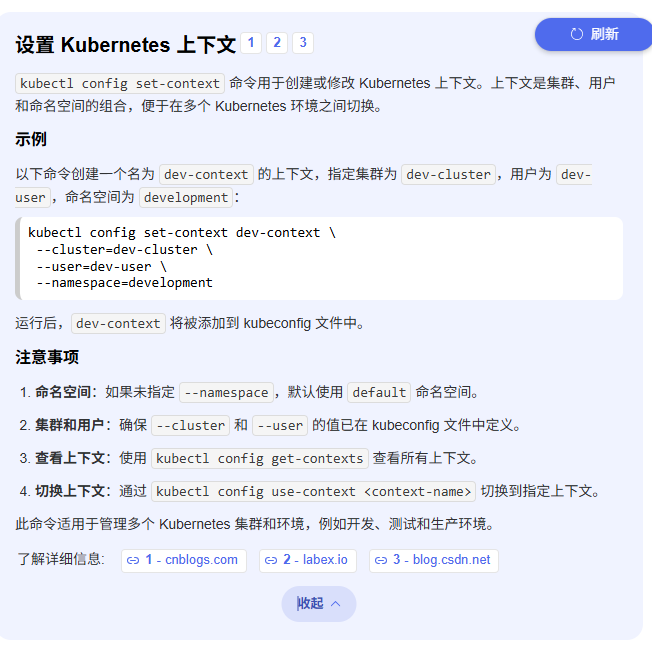
3. 合并配置文件 在 Kubernetes 环境中,使用 kubectl 管理多个集群非常常见。通过配置 kubeconfig 文件,可以轻松切换和管理多个集群。以下是实现方法的详细步骤。
方法 1: 合并多个配置文件
KUBECONFIG=/.kube/config1:/.kube/config2 kubectl config view –merge –flatten > ~/.kube/config
kubectl config view
方法 2: 配置环境变量
设置环境变量 将多个配置文件路径添加到 KUBECONFIG 环境变量中:
export KUBECONFIG=/.kube/config:/.kube/test-config
kubectl config get-contexts
方法 3: 手动编辑配置文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 apiVersion: v1 clusters: - cluster: server: https://127.0.0.1:6443 name: cluster1 - cluster: server: https://192.168.0.1:6443 name: cluster2 contexts: - context: cluster: cluster1 user: user1 name: context1 - context: cluster: cluster2 user: user2 name: context2 current-context: context1
切换集群上下文
通过以上方法,您可以轻松管理多个 Kubernetes 集群,提高运维效率。
大家好!在 云原生 的世界里,和 Kubernetes 打交道是家常便饭。如果我们像我一样,需要同时管理多个 Kubernetes 集群——比如一个用于严谨发布的 生产环境 ,一个用于大胆实验的 测试环境 ,甚至还有本地开发环境——那么高效、安全地在它们之间切换就成了必备技能。
很多朋友(包括我自己有时也会!)可能会因为一段时间没用而忘记 kubectl 中那些用于切换配置的命令。别担心,这很正常!今天,我们就来系统地回顾一下 kubectl 配置管理的核心概念—— 上下文(Context) ,以及如何利用它在不同集群间自如切换。
核心概念:kubeconfig 文件与上下文(Context) kubectl 的所有配置信息都存储在一个或多个 YAML 文件中,默认情况下是 $HOME/.kube/config 。这个文件我们通常称为 kubeconfig 文件。把它想象成我们的 Kubernetes “护照”,里面记录了我们能访问哪些集群,用什么身份访问。
一个 kubeconfig 文件通常包含三个主要部分:
Clusters(集群) :定义了我们要连接的 Kubernetes 集群的信息,比如 API Server 的地址和集群的 CA 证书。Users(用户) :定义了访问集群所使用的凭证,可能是用户名/密码、Token 或客户端证书。Contexts(上下文) :这是连接 集群 和 用户 的桥梁。一个 Context 定义了使用哪个 User 凭证去访问哪个 Cluster。
关键点: 我们可以通过切换 Context 来改变 kubectl 当前操作的目标集群和使用的身份。
管理 kubeconfig 的常用 kubectl config 命令 kubectl 提供了一套 config 子命令来帮助我们查看和管理 kubeconfig 文件。以下是几个最核心、最常用的命令:
1. 查看当前配置:kubectl config view 这个命令会显示我们当前的 kubeconfig 文件内容(或者合并后的内容,如果我们配置了多个文件)。它会隐藏敏感信息(如证书和 Token 的具体内容),非常适合快速检查配置概览。
1 2 kubectl config view bash1
如果我们想看某个特定 Context 的详细信息,可以加上 --context 参数:
1 2 3 kubectl config view --context=prod-cluster bash12
2. 列出所有可用的上下文:kubectl config get-contexts 这是 最常用 的命令之一,它会列出我们在 kubeconfig 文件中定义的所有 Context。当前正在使用的 Context 会在名称前用星号 * 标记。
1 2 3 4 5 6 7 kubectl config get-contexts bash123456
从上面的输出可以清晰地看到:
当前激活的 Context 是 test-cluster 。
还有名为 prod-cluster 和 docker-desktop 的 Context 可供切换。
3. 查看当前使用的上下文:kubectl config current-context 如果我们只想快速确认当前 kubectl 命令会作用于哪个 Context(哪个集群),这个命令最直接:
1 2 3 4 kubectl config current-context bash123
4. 切换上下文:kubectl config use-context 这绝对是 核心中的核心 !当我们需要将 kubectl 的操作目标从一个集群切换到另一个集群时,就使用这个命令。
假设我们想从当前的 test-cluster 切换到 prod-cluster :
1 2 3 4 kubectl config use-context prod-cluster bash123
切换成功后,我们可以再次使用 kubectl config current-context 或 kubectl config get-contexts 来验证当前上下文是否已更改。
1 2 3 4 5 6 7 8 9 10 11 kubectl config current-context kubectl config get-contexts bash12345678910
现在,所有后续的 kubectl 命令(如 kubectl get pods, kubectl apply -f ... 等)都会默认发送到 prod-cluster 所定义的集群,并使用 user-prod 的身份进行认证。
实践场景:在生产和测试集群间切换 假设我们的 kubeconfig 文件中已经配置好了代表生产环境和 测试环境 的 Context,可能分别命名为 production 和 testing 。
我们的日常操作流程可能是这样的:
检查当前在哪: 1 2 kubectl config current-context bash1
1 2 kubectl config get-contexts bash1
需要操作测试环境: 1 2 3 4 5 6 kubectl config use-context testing kubectl config current-context kubectl get pods -n test-namespace bash12345
需要紧急处理生产环境问题: 1 2 3 4 5 6 kubectl config use-context production kubectl config current-context kubectl get deployment -n critical-app bash12345
完成生产环境操作,切回测试环境继续工作: 1 2 kubectl config use-context testing bash1
提升效率的小贴士
清晰命名 Context :给我们的 Context 起一个能清晰表明环境和用途的名字,比如 gke-prod-eu, eks-dev-us, local-minikube 等。避免使用模糊不清的名字。使用 Shell 别名 :很多人喜欢为 kubectl 设置别名,比如 alias k=kubectl 。这样我们的命令可以更短: k config get-contexts, k config use-context my-context 。考虑使用辅助工具 :社区有一些流行的小工具可以让我们更方便地切换 Context 和 Namespace,例如:
kubectx (用于切换 Context)kubens (用于切换 Namespace)
注意 kubeconfig 文件的安全性 : kubeconfig 文件包含了访问集群的凭证,务必妥善保管,不要泄露给未授权的人员。
总结 管理多个 Kubernetes 集群配置并不复杂,核心就在于理解和运用 kubeconfig 文件中的 Context 概念。通过掌握 kubectl config 的几个关键子命令:
view: 查看配置概览get-contexts: 列出所有可用上下文current-context: 显示当前激活的上下文use-context <context-name>: 切换到指定的上下文
我们就能轻松地在不同的 Kubernetes 环境(如生产和测试)之间安全、高效地切换了。希望这篇回顾能帮我们重新找回操作 kubectl 多集群配置的熟悉感!